Discover the $10.5 Trillion Cybercrime Economy. Digital space of the year 2025 is the border of an uncharted danger. The medical sector itself has been put directly at risk due to the Change Healthcare breach in early 2024 that has directly affected 193 million people people. This one incident revealed the clinical accessibility, financial information and personal existence of almost two-thirds of the American population. It is a sharp lesson on how one weakness in one important node can bring down an industry.
Nowadays, the magnitude of such threat is in trillions. By the year 2025, the economy of cybercrime in the world will have reached a phenomenal figure of 10.5 trillion dollars. This is estimated to mean that a cybercrime is ranked as the 3rd largest economy in the world to the United States and China in terms of gross domestic product. As you read this sentence, about seven patterns of data breach take place on earth. The regular occurrence of these attacks subjects each citizen who can be connected to a continuous low level radiation of danger.
This relentless rate can be seen in data provided in the first half of 2025. According to the data given by Secureframe, 166 million people were victims of data breaches in the first six months of the year alone. In 2024, Bright Defense Diet monitored more than 5,176 established breaches in which sensitive information was shifted off safe servers to the possession of unscrupulous entities. Cybersecurity Ventures estimates that this expenditure is only going to increase, as hacking groups become organized, and illegal technology gained through automation.
Table of Contents
Data Breach Landscape

The modern data theft is a work in the industrial efficiency as its architecture. Companies and thieves have entered into a high-stakes equilibrium.
How much Data Breach Landscape Cost?
The existing market prognosis indicates a changing economical condition of the breached entities. By 2025, the average cost of a data breach was reduced to 4.44 million, which is 9 percent lower than the total cost of data breach in 2024. This is a decline after a spate of aggressive investment into automated detection and incident response systems.
At the same time, the exposure period is becoming smaller. The average duration to detect and seal a breach has reduced to 241 days. This record low of nine years is an indication that defensive technologies are working to seal the dwell time window that attackers enjoyed before. The amount of theft data raw material is, however, skyrocketing. A huge number of compromised accounts is revealed by Surfshark, rising by close to eight times between the 730 million in 2023 and exceeding 5.5 billion in 2024.
Who is Affected The Most by Cybercriminals?
Industry-specific evidence indicates the monetary motives of these attacks. The healthcare industry is the most profitable one to the cybercriminals. The average cost of breaches in this sector is 7.42 million. The fact that medical history is indelible, and thus an indispensable and priceless asset in the dark web.
Close behind are financial services which are attacked. In 2024, 737 compromises of this industry were reported, and it was the most attacked commercial arena. There are three main regions in which the activity is concentrated as geographically analyzed. The densities of highest breaches are associated with Russia, France, and the United States. Such countries are the location of the digital infrastructure and affluence that draws the most advanced threat actors in the world.
What Cyber Criminals Do With Stolen Information In Dark Web?

The route to a safe database to a dark web market is executed by a professional pipeline of four stages that are strictly adhered to.
Phase 1: The Breach (Initial Access)
Cyberspace attackers will take the path of least resistance. According to Bright Defense 53 percent of breaches are caused by stolen credentials. By 2025, the character of such attacks has been changed by incorporating the element of artificial intelligence. 1 out of 6 attacks incorporate artificial intelligence and sophisticated phishing and authentication filters can be used on scale. Regardless of such improvements, organizations are more quickly putting this to a containment and a 2024 average time of 64 days.
Phase 2: Data Exfiltration
After gaining access, it is targeted to discharge the valuable information quickly. Large amounts of data are targeted by the criminals in order to have a high ROI. This volume is a case study of a Change Healthcare breach where the hackers were able to steal 6 terabytes of data. This shipment contained names, Social Security numbers and in-depth clinical histories.
Phase 3: Initial Access Brokers (IABs)
The contemporary criminal economy involves the use of a professional intermediary called the Initial Access Broker. These are actors who concentrate on gaining accessibility to networks and later sell the accessibility to the highest bidder. Darknet marketplaces cost between $100 and list small business accreditation and above 200,000 to list with major corporate networks. Such brokers represent the crucial connection that allows specialized ransomware groups to attack without necessarily doing the initial reconnaissance themselves.
Phase 4: Dark Web Marketplaces
the dark web marketplaces are the last place of stolen information. such systems use advanced escrow and reputation systems to enable trust between the anonymous criminals. According to DeepStrike, about 20-25 billion dollars of the cryptocurrency, including Bitcoin and Monero, is involved in these markets every year. By 2025, such market places replicate credible e-commerce platforms by providing search functions, volume purchasing offers, and 24/7 customer services on customers who purchase stolen information.
The Dark Web Price Index 2025 | Data Pricing in Dark Web Marketplaces

Data stolen might be worth something depending on how useful, fresh and complete it is. The following tables were used to provide the current market rates to your digital identity.
Personal Identification Data Pricing in Dark Web Marketplaces
| Item | Market Price (USD) | Source |
| U.S. Social Security Number | $1 – $6 | DeepStrike |
| Full Identity Profile (Fullz) | $20 – $100 | DeepStrike |
| Driver’s License Scan | $20 – $25 | Dark Market Avg |
| Passport Scan | $15 – $35 | Dark Market Avg |
| Electronic Medical Record (EMR) | $100 – $350 | Keeper Security |
Financial Data Pricing in Dark Web Marketplaces
| Item | Market Price (USD) | Source |
| Credit Card with CVV | $10 – $40 | DeepStrike |
| Banking Credentials ($100 Min. Bal) | $35 | PrivacySharks |
| PayPal Account ($12,000 Val) | $1,200 | PrivacySharks |
| Verified Crypto Exchange Account | $100+ | PrivacySharks |
Premium Corporate Access Data Pricing in Dark Web Marketplaces
| Access Type | Market Price (USD) |
| Corporate VPN Credentials | $500 – $5,000 |
| Domain/Cloud Administrator Access | $10,000 – $50,000+ |
| Corporate Database Access | $5,000 – $50,000 |
Pricing Variables in Dark Web
The final sale price of a data set is determined by a number of variables. The most important element is freshness; the most recent data on a breach is priced higher than an entry made three years ago. Value also goes hand in hand with completeness since a Fullz profile that includes an SSN, date of birth, and address is more useful in committing fraud than an email address by itself. The demand is also determined by the geographic origin as a U.S. or EU data attracts a higher price as the credit limit and insurance payout is higher in these geographies. Lastly, verification status and account balance of financial data are the direct multipliers of the asking price.
The CyberCrime Ecosystem
The cybercrime industry has a decentralized franchise model economy. This association enables individual specialists to work on big attacks without necessarily having to come into contact with each other physically.
Cyber Criminals Roles in CyberCrime Ecosystem
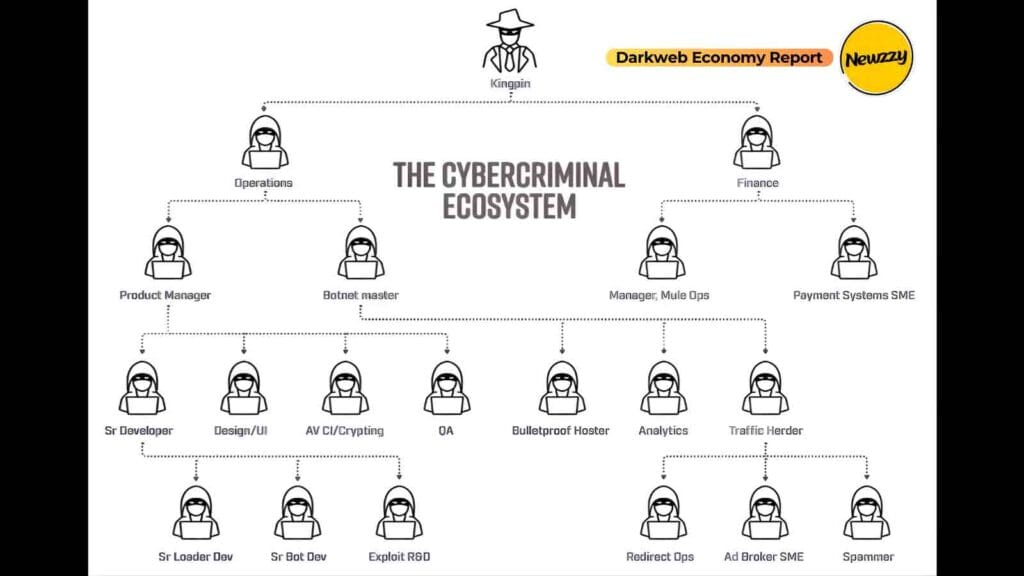
There are a number of roles in the ecosystem. The entry points are discovered by the Initial Access Brokers (IABs). The operators of the ransomware-as-a-Service (RaaS) produce the malicious code and sell it to affiliates as a percentage of the ransom. Stealing information is controlled by data brokers and data resellers. Cryptocurrency mixers assist money launderers in obscuring the source of illegal money. Lastly, service providers that provide specialized services have opened up bulletproof hosting and encrypted communication channels to conceal the operation against the law enforcers.
CyberCrime Business Model Analysis
The cybercrime is an industry with high growth with an increase of 15 percent every year. According to DeepStrike research, of all the items that are present in dark web markets, 65 percent of them are identity-related. The developmental aspects of revenue distribution of these criminal groups tend to settle to the benefit of the developers, yet the ease with which any individual can be an affiliate is sustaining the workforce.
The recent case studies highlight the strength of this model. Cl0p ransomware group used a bug in MOVEit file transfer software to affect 95 million individuals. The Russian underground has persisted in creating the best malware described as stealer, which automatically gathers credentials of millions of infected computers. These organizations operate with discipline and hierarchy of the contemporary tech companies.
Who’s Buying The Stolen Information From Dark Web And Why
There are four major buyer categories in the need of the stolen data. The information is used in particular, high-profit criminal results of each group.
Buyer Categories
The identity thieves form the highest segment of the market. They purchase Fullz to get new lines of credits or secure loans under the name of a victim. Fraudsters are interested in transactional theft, where stolen credit cards are used to make the massive purchase of retail goods or gift cards programs. The actors or agents of a nation-state use the information to conduct espionage or to establish databases on the citizens of other countries in case of future activities involving intelligence. Corporate espionage agents will steal the trade secrets of their competitors by hacking into their intellectual property and cloud administration usernames.
How CyberCriminals Use Stolen Data?
The uses of this data are various. Account takeover attacks are carried out by attackers, which aim to steal social media, email, and financial accounts. They perform tax fraud and refund scams by submitting promptly on the tax season with the stolen SSN. The fraud of medical insurance implies use of EMR of a victim to obtain costly treatment or prescriptions. Corporate infiltration is a practice that is based on stolen VPN credentials used to plant the backdoors in secured networks. Lastly, the social engineering campaigns utilise stolen personal data to produce most believable falsehoods that exploit the workers into transferring huge amounts of money.
A digital document turns into an actual tragedy through its effecting chain. Stolen SSN will result in frozen bank account thus preventing a mortgage payment and ultimately causing complete ruin of financial position of a victim.
How Law Enforcement Responses to CyberCrime?
It is a worldwide drive to destroy the digital underworld by governments. Even major breakthroughs in the recent years demonstrate that there is no market which can be discussed as absolutely impregnable.
Major Takedowns by Law Enforcements in CyberCrime Ecosystem
In 2023, the Genesis Market was closed down by law enforcers, which was a great success. This was further accompanied by the sealing of the Hydra Market in 2022, then the largest dark web marketplace in the world. Most recently, in June 2025, a coordinated operation resulted in the Canada-led take-down of the BidenCash system, taken down 145 domains and millions of dollars of cryptocurrency related to the distribution of 15 million credit card numbers.
Challenges and Successes of Law Enforcements
Irrespective of such victories, there is still the same probability of apprehension and conviction at only 0.05 percent in the United States. International border shoppers take advantage of the jurisdiction challenges by having their activities hosted by the countries that do not extradite cyber-criminals. Anonymity of the cryptocurrency and the speed of market re-emergence is such that every site that has been removed is replaced by two more in a few weeks.
Nonetheless, global collaboration programs and high-quality blockchain analysis software is becoming effective. The agencies can track the face behind the handle by conducting an undercover activity that penetrates the trust groups of these markets.
How to Protect Data From Cyber Attacks?
Defense in 2025 needs to change the attitude traditionally adopted as having a perimeter to one of having a zero-trust attitude.
For Individuals
To have a secure digital life, you need first a number of tools. Dark web surveillance technologies will notify you when your email or SSN is listed in a criminal marketplace. Freezes of credit stop identity thieves. Password management and hardware-based 2FA (including YubiKeys) prevent the possibility of credentials theft. This can be done by checking every now and then whether your data has been breached by using reliable breach databases that will immediately have the action rectified.
For Organizations
The corporate defense is based on speed and checking. Firms with AI-based security systems discover intrusions 108 days earlier than their counterparts and can save an average of one point seven six million dollars. The use of a Zero-trust architecture presupposes that all users and devices can be dangerous, and every access request should be verified. Training employees, selecting an incident response plan, and purchasing cyber insurance would supply the resiliency to survive an unavoidable attack. Learn more about Data protection.
The Future of the Data Economy
Five years down the line will be characterized by an arms race between attackers and defenders enhanced with AI.
Emerging Trends in Data Breach
By 2025, one out of every 6 breaches is already AI-related. There is an increase in deepfake and synthetic identity fraud, in which criminals construct new individuals entirely by mixing authentic stolen information with AI-generated characteristics. The computation of quantum computing presents a threat to encryption standard of today, which then moves towards post-quantum level of security. Furthermore, the biometric data market is also coming into existence with the use of fingerprints and facial scan becoming a key to our online identity.
Projections and Opinions of Experts About Data Breach
By 2030, it is another more controlled data environment which analysts project. There is however the possibility of a market crash in case the amount of stolen data will reach very high levels that its value will be zero. According to experts, technology solutions are going to evolve, but the most vulnerable point on the chain will still be the human one.
Conclusion About CyberCrime Economy
Cybercrime economy is a structural reality of the modern world and is estimated to cost the nation as much as 10.5 trillion dollars. It is a full blown and professionalized, and a highly lucrative business that sells your personal information like a commodity. The sheer size of the breach such as Change Healthcare indicates that no institution is too big to fail.
Nevertheless, the awareness is the initial defense. You can make your information unprofitable to the attacker by appreciating the worth of your data and applying a multi-layered security strategy because then making the cost of attacking more expensive than the objective.

